On the safe side of healthcare software
We help you to keep sensitive patient information safe and comply with regulations.
Minimize the risk of data breaches by identifying and remediating vulnerabilities in an organization’s IT systems, applications, policies and procedures.
Key numbers
Our case studies
Team size: 3 developers
Team size: 5 developers
Team size: 4 developers
Team size: 4 developers
Team size: 3 developers
Our clients say
Total reviews
43
Average rating
Source


Artem Arutyunyan
Head of Digital at Media Development Foundation
“With our High-load News Media project, we have reached our goals to increase analytics by rebuilding the infrastructure, boosting the performance of the website, and improving the news cloud panel for our journalists. Hromadske.ua is extremely thankful and satisfied with the costs spent since the results we gained are perfect.”

Jeff Wallace
Co-Founder at Silicon Valley in Your Pocket
“We are thrilled to have such a knowledgeable, skilled and collaborative team in Ralabs as we build our business into the future. They helped us to create an excellent solution, one that met our early pilot needs but that was also scalable to meet our long-term requirements.”

Ian Atkins
Co-Founder & COO at Choosing Therapy
“Ralabs truly cared about the products being built and the mission of ChoosingTherapy.com. Working with Ralabs feels like your working with an extension of your own team. Every team member was invested in our mission.”

Jonas Bertelsen
Chief Product Officer (CPO) at Cludo
“Working with the team was an experience in precision, expertise, and dedication. Their technical acumen ensured our GPT-Powered Q&A Chat was not only functional but ahead of the curve. We are proud to have collaborated with such a proficient team.”

Sam O’Brien
Product Lead at Fillit
“We were immediately impressed by Ralabs technical skill and expertise; however, it was their commitment and professionalism that assured us we had chosen the right partner. We feel confident taking on new projects as we know Ralabs can provide the skills we need with relatively short notice!”

Gil Plotnizky
Co-Founder and Director at Equilibrio
“We had an amazing experience working with Ralabs.org on our website from day one, their team was professional, efficient, and truly understood our needs—covering everything from design to operations, reservations, and financial integrations with third-party software.”
Healthcare data security services we offer
Security assessment
Protect your business against cyber attacks and ensure that sensitive information is not accessed, used, disclosed, disrupted, modified, or destroyed. A security assessment will identify any areas of weakness and provide guidance on how to address them with several levels of protection.
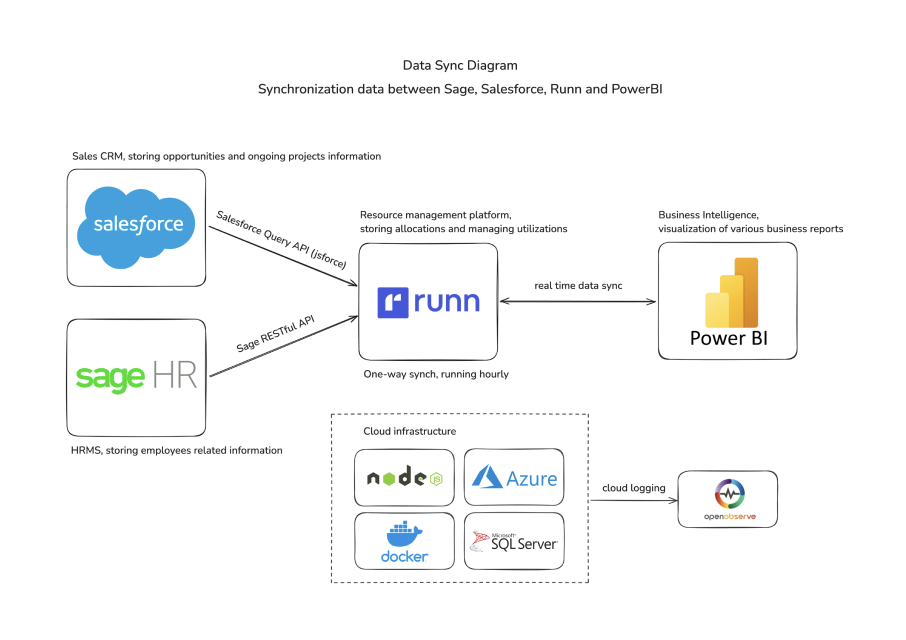
Cloud infrastructure security
We provide tech consultations on the confidentiality, integrity and availability of a healthcare provider’s cloud resources and sensitive data. The team will assess the current security state and recommend measures and best practices to secure the cloud environment.
Regulatory compliance
Stay compliant with regulations such as HIPAA, GDPR and CCPA. A compliance assessment can help you understand your responsibilities and identify any areas where changes may be necessary to ensure compliance with these regulations.
Authentication & access control
2-factor authentication and access control are security measures that are used to control access to sensitive patient information within a healthcare organization. Avoid unauthorised access to patient data and ensure that only authorised users can access sensitive patient information and electronic health records.
End-to-end IT security testing
Identify and evaluate potential vulnerabilities in software, IT infrastructure, policies and procedures. By detecting, analyzing and helping to remediate any flaws, and human errors, quality assurance services help organizations prevent security breaches and stay compliant with regulations.
Apply security best practices, tools, and testing into the software development lifecycle from the beginning.
Integrate security into your software development process
From the start identify and integrate security requirements into the overall software structure. Specify any security regulations or healthcare data security standards that the software must adhere to.
When developing software for the healthcare industry, it’s vital to follow industry-specific security guidelines and protocols to ensure the protection of sensitive patient information.
For features that are yet to be ideated, designed, and developed. For up-and-running products that are to be maintained, put through security tests, and updated regularly.
To deploy software, there must be a secure environment. Use access management controls, encryption and regular security audit to enhance security in a deployed environment.
Regularly update and patch healthcare software to address new security vulnerabilities as part of an ongoing healthcare cybersecurity process
Benefits
Keep patient data protected at all times
Meet all the compliance criteria
Maintain patient trust
Be resilient to cyber attacks and threats
Provide secure remote access
Prevent security breaches
Improve patient care
Ensure interoperability
Regulations and standards we work with




Enhanced security for the dental system
We overhauled the outdated system for dental referrals, enhanced its security, resilience, and improved the overall performance.
The app is being turned into a full-scale platform, reliable for preserving and managing the patients’ sensitive data. Also, the AWS migration process led to improved app efficiency.
Related publications
FAQ
The biggest security threat to healthcare data is often considered to be cyber attacks such as hacking, phishing, and malware. These types of attacks can compromise sensitive patient information such a medical records and lead to data breaches.
Data loss during migration operations or data processing in healthcare can pose a significant cybersecurity risk. To mitigate these risks, healthcare organizations should implement robust security measures, such as encryption and secure data transfer protocols, and conduct thorough testing before and after any migration or data processing operations.
Additionally, they should have incident response plans in place to quickly and effectively respond to any security breaches that may occur.
Lack of employee training, weak passwords, and outdated systems and software can also contribute to the risk of a data breach in the healthcare industry.
Healthcare organizations can protect patient data by implementing a number of security measures. Such as regular security assessments, proper employee training, incorporating the best practices of quality assurance and keeping up to date with industry standards and regulations.
Also, implementing backup and rollback best practices can help mitigate the risk of data loss during migration operations or data processing in healthcare.
- Regularly update software and firmware.
- Implement network segmentation.
- Use strong authentication.
- Conduct regular security assessments.
- Provide employee training.
- Follow industry standards and guidelines.
- Regularly monitor the network for unusual activity.
- Implement secure communication protocols.